The cr-gpg extension for Chrome/Gmail consists of a couple of html/js files + a native .dll/.so/.dylib that basically was an interface for calling the console command gpg (in old version), or for GPGME (current/new version).
So I guess "calling the console command" spoils the surprise - yes, a few of these bugs were shell injections in various places. The most interesting one was the recipient e-mail address in case of replying to an e-mail and encrypting it - you can set the Reply-To: field to anything of course - kudos to Tavis for this idea (my ideas were a MITM scenario with http://mail.google.com - see other bugs; or an XSS on said site invoking the plugin).
E.g.: Reply-To: `echo${IFS}blabla`@gmail.com. See also some pictures below (click to zoom).
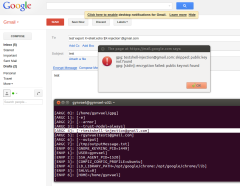
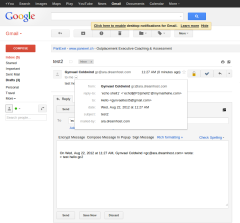
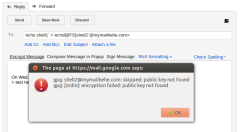
The rest of the bugs were:
* While encrypting an e-mail, the /tmp/outputMessage.txt had -rw-rw-r-- rights. Please remember, that it's encrypted; the only thing it could be used for is learning who is the e-mail to, in case the attacker/sniffer can match the key ID. So this was a minor privacy issue at most.
* The manifest allowed http://mail.google.com/ to use cr-gpg. This might aid an attacker in a MITM scenario (MITM → redirect any page to http://... → JS → shell exec).
* (Discovered later): XSS in message body (well, you decrypt the message and u get XSSed; kinda bad).
Anyways, this all is fixed now in 0.8.2 (it's still considered to be alpha btw).
Timeline:
* 22 Aug 2012 - initial report; ack from the cr-gpg guys (thinkst.com)
* 01 Sep 2012 - most fixed; reported the XSS
* 16 Sep 2012 - all fixed in repository
* 26 Sep 2012 - 0.8.2 officially out
The authors were really responsive and fixed the issues fast. Kudos for that :)
Two more things:
1. The authors were working on GPGME version of cr-gpg at the time of report anyways, so the shell injections would be fixed even without me reporting this.
2. Funny story - Krzysztof Kotowicz (Hi ;>) discovered and reported the shell injections and XSS c.a. at the same time. He also showed these bugs today on a conference in Belgium.
Changed in 0.8.2 :
Fixed a number of security issues reported by both Gynvael Coldwind (http://gynvael.coldwind.pl/) and Krzysztof Kotowicz (http://blog.kotowicz.net/)
[...]So if you're testing this (still alpha), be sure to update.
By the way...
If want to improve your binary file and protocol skills, check out the workshop I'll be running between April and June → Mastering Binary Files and Protocols: The Complete Journey
UPDATE: Krzysztof Kotowicz published a detailed write-up about cr-gpg bugs on his blog.
Cheers,









Comments:
Same, congratz :)
I've added a link to said post above - it's a cool write-up.
Add a comment: