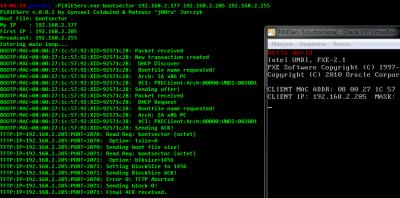
 A few years back, we've been (i.e. j00ru and Gynvael) working on a bootkit-related project (some polish SecDay'09 presentation slides can be found here: Bootkit vs Windows.pdf). One of its basic requirements was the ability to load custom boot-"sectors" from an external host in the local network. Since the publicly available solutions required too much time to be spent on configuration and we didn't need most of the offered functionality anyway, we decided to create an extremely simplified Preboot Execution Environment (PXE) server on our own, and so PiXiEServ came to be. Actually, a great majority of the source code was written by Gynvael, with only few modifications applied by me (i.e. j00ru).
A few years back, we've been (i.e. j00ru and Gynvael) working on a bootkit-related project (some polish SecDay'09 presentation slides can be found here: Bootkit vs Windows.pdf). One of its basic requirements was the ability to load custom boot-"sectors" from an external host in the local network. Since the publicly available solutions required too much time to be spent on configuration and we didn't need most of the offered functionality anyway, we decided to create an extremely simplified Preboot Execution Environment (PXE) server on our own, and so PiXiEServ came to be. Actually, a great majority of the source code was written by Gynvael, with only few modifications applied by me (i.e. j00ru).Although we eventually haven't managed to complete the said bootkit-related project and the server source code is dated back to October 2009, we've now decided that the program and its sources might prove useful to other people playing with the network machine booting mechanism, as well as trying to write their own OS and test it on both virtual and real hardware (without having to worry about getting old school floppies, CDs, etc).
Please, however, bear in mind that the application only provides the most basic functionality (i.e. it allows serving a single file via TFTP and so doesn't support multi-step/multi-file booting) and doesn't support the other advanced features described in the PXE specification. So, while PiXiEServ can be helpful with minor research/etc activities, you won't be able to perform a complete OS installation using it (I use it also for development/testing of a pet OS called OSAmber).
We've successfully used PiXiEServ with VirtualPC and VirtualBox, as well as a couple of different laptops, netbooks and PCs.
If you are using Windows Vista (2003?) or later you will need to input the broadcast address specific to your local network as the fourth command line parameter (e.g. 192.168.1.255 if you are in a 192.168.1.0 network with 255.255.255.0 mask) - this is due to some change in networking made in Vista (2003?) and since it's an old project we didn't want to spend to much time on this.
A package containing Windows executables and source code can be downloaded from here (PiXiEServ.zip, 56 kB)
Note: The project also works on the GNU/Linux platform.
By the way...
If want to improve your binary file and protocol skills, check out the workshop I'll be running between April and June → Mastering Binary Files and Protocols: The Complete Journey
Should you encounter any problems with the compilation or correct functioning of the program, feel free to drop a line either to me or j00ru.
Have fun!
P.S. English language is funny - "bear in mind", lol.









Add a comment: