The
CONFidence Teaser CTF 2016 by Dragon Sector is now over and the results are in (congratz 9447!). Therefore I decided to share the sources of my task called ReRe, which was a Python rainbow-heavy obfuscation-heavy bytecode-all-around challenge. I won't spoil too much in case you would like to try to solve it (crackme/rere.py in the archive), but if you would like to read more on it, just see the SOLUTION.md file in the zip file. I'll add, that the obfuscation used self-modifying bytecode, some bytecode-level obfuscation and minor string obfuscation as well, so if you would like to learn more about Python 2.7 internal code representation, try your luck with ReRe :) It was solved 5 times btw.
Download:
confidence-teaser-2016-ds-gynvael-rere.zip"Video":
rere_anim.gif (a 3 MB gif, you have been warned)
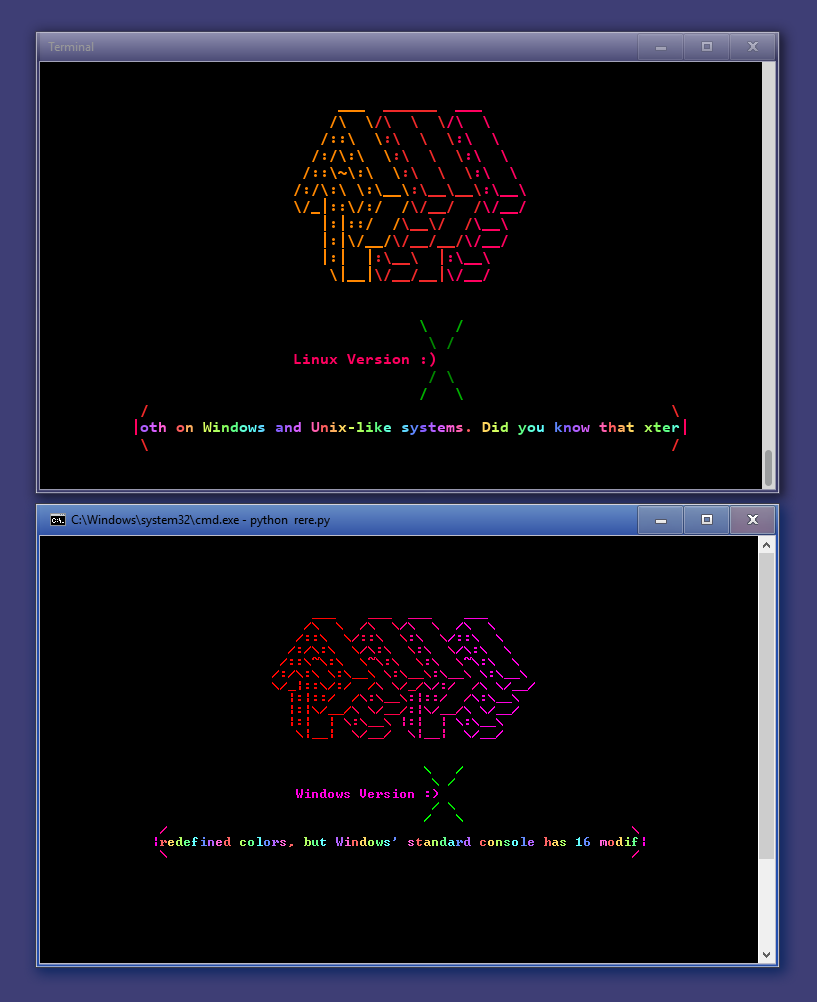
Have fun, good luck!


Comments:
I'll ask the author (KeiDii) about it :)
https://github.com/k3idii/ctf_task_aMazeing
end
One team after the CTF according to IRC logs. No write-up yet though.
Probably yet another write-up but https://github.com/mr6r4y/re-write-ups/tree/master/crackmes/ReRe_by_Gynvael/solution
Add a comment: