 While writing an article on how "Hello World" actually works in Python (written with j00ru and Adam Sawicki, and published in 100th issue of the Polish Programista magazine; we'll publish the English translation on our blogs around September/October 2022) I've played a bit with Python's ast module (as in Abstract Syntax Tree) and decided it would make a cool CTF challenge if I would make some restrictions on AST level and have folks try to bypass it.
While writing an article on how "Hello World" actually works in Python (written with j00ru and Adam Sawicki, and published in 100th issue of the Polish Programista magazine; we'll publish the English translation on our blogs around September/October 2022) I've played a bit with Python's ast module (as in Abstract Syntax Tree) and decided it would make a cool CTF challenge if I would make some restrictions on AST level and have folks try to bypass it.
This wasn't of course the first challenge using AST on a CTF, though I did think to check only after I've already implemented it. Thankfully other challenges use different restrictions, so there was no collisions. Here are some of them though (leave a comment in case I've missed some):
- pysandbox @ TokyoWesterns CTF 4th 2018 (example write-up by hawkcurry),
- Tree of danger @ HTB Uni CTF 2021 - Quals (example write-up by Ratman),
- Finance Calculat0r 2021 @ CyberSecurityRumble CTF 2021 (example write-up by Zeyu).
Eventually the challenge was published at Google CTF 2022 in the Sandbox category under the name of Treebox and was solved 268 times, making it the easiest (or most popular? ;>) challenge of the CTF.
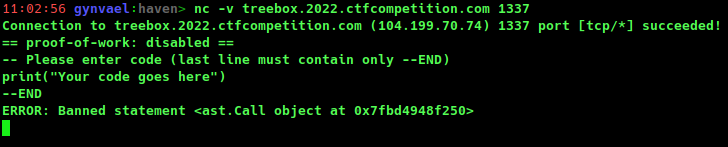
The challenge is likely still online when you're reading this blog post (if it's not, let me know) and you need only netcat to enjoy it. Just follow the link above, download the source code and have fun!
There are only 3 AST-level restrictions in Treebox:
- you can't call a function,
- you can't use import,
- and you can't use import from.
What was wonderful about the way players solved it, was that every solution was unique in some way. There were of course clusters of solutions converging around this or that feature, but at the end of the day the solutions were pretty different.
By the way...
If want to improve your binary file and protocol skills, check out the workshop I'll be running between April and June → Mastering Binary Files and Protocols: The Complete Journey
Since the solutions contain spoilers, I've posted them in a separate note in case readers would like to try their luck first.
Warning SPOILERS: Treebox solutions (it's at the bottom of this set of notes)
Whether you try the challenge first or now, if you enjoy Python I greatly recommend looking at the solutions. They are extremely clever in some cases, and fun in every case.
Have fun!









Add a comment: